[February-2023]350-201 PDF Exam Dumps 350-201 142Q Instant Download in Braindump2go[Q46-Q76]
February/2023 Latest Braindump2go 350-201 Exam Dumps with PDF and VCE Free Updated Today! Following are some new Braindump2go 350-201 Real Exam Questions!
QUESTION 46
A new malware variant is discovered hidden in pirated software that is distributed on the Internet. Executives have asked for an organizational risk assessment. The security officer is given a list of all assets. According to NIST, which two elements are missing to calculate the risk assessment? (Choose two.)
A. incident response playbooks
B. asset vulnerability assessment
C. report of staff members with asset relations
D. key assets and executives
E. malware analysis report
Answer: BE
Explanation:
https://cloudogre.com/risk-assessment/
QUESTION 47
Refer to the exhibit. At which stage of the threat kill chain is an attacker, based on these URIs of inbound web requests from known malicious Internet scanners?
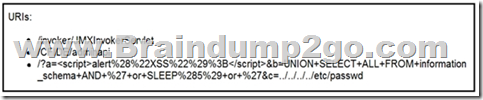
A. exploitation
B. actions on objectives
C. delivery
D. reconnaissance
Answer: C
Explanation:
https://www2.deloitte.com/content/dam/Deloitte/sg/Documents/risk/sea-risk-cyber-101-july2017.pdf
QUESTION 48
What should a security analyst consider when comparing inline traffic interrogation with traffic tapping to determine which approach to use in the network?
A. Tapping interrogation replicates signals to a separate port for analyzing traffic
B. Tapping interrogations detect and block malicious traffic
C. Inline interrogation enables viewing a copy of traffic to ensure traffic is in compliance with security policies
D. Inline interrogation detects malicious traffic but does not block the traffic
Answer: A
QUESTION 49
Refer to the exhibit. Which two steps mitigate attacks on the webserver from the Internet? (Choose two.)
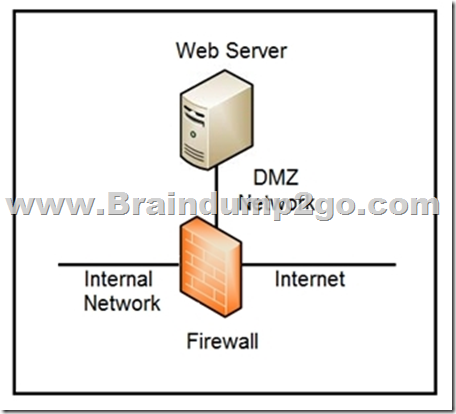
A. Create an ACL on the firewall to allow only TLS 1.3
B. Implement a proxy server in the DMZ network
C. Create an ACL on the firewall to allow only external connections
D. Move the webserver to the internal network
E. Move the webserver to the external network
Answer: AB
QUESTION 50
According to GDPR, what should be done with data to ensure its confidentiality, integrity, and availability?
A. Perform a vulnerability assessment
B. Conduct a data protection impact assessment
C. Conduct penetration testing
D. Perform awareness testing
Answer: B
Explanation:
https://apdcat.gencat.cat/web/.content/03-documentacio/Reglament_general_de_proteccio_de_dades/documents/DPIA-Guide.pdf
QUESTION 51
A payroll administrator noticed unexpected changes within a piece of software and reported the incident to the incident response team. Which actions should be taken at this step in the incident response workflow?
A. Classify the criticality of the information, research the attacker’s motives, and identify missing patches
B. Determine the damage to the business, extract reports, and save evidence according to a chain of custody
C. Classify the attack vector, understand the scope of the event, and identify the vulnerabilities being exploited
D. Determine the attack surface, evaluate the risks involved, and communicate the incident according to the escalation plan
Answer: B
QUESTION 52
A company recently completed an internal audit and discovered that there is CSRF vulnerability in 20 of its hosted applications. Based on the audit, which recommendation should an engineer make for patching?
A. Identify the business applications running on the assets
B. Update software to patch third-party software
C. Validate CSRF by executing exploits within Metasploit
D. Fix applications according to the risk scores
Answer: D
Explanation:
Cross-Site Request Forgery (CSRF) is a type of attack that occurs when a malicious web site, email, blog, instant message, or program causes a user’s web browser to perform an unwanted action on a trusted site when the user is authenticated. A CSRF attack works because browser requests automatically include all cookies including session cookies. Therefore, if the user is authenticated to the site, the site cannot distinguish between legitimate authorized requests and forged authenticated requests.
QUESTION 53
An engineer is analyzing a possible compromise that happened a week ago when the company database servers unexpectedly went down. The analysis reveals that attackers tampered with Microsoft SQL Server Resolution Protocol and launched a DDoS attack. The engineer must act quickly to ensure that all systems are protected. Which two tools should be used to detect and mitigate this type of future attack? (Choose two.)
A. firewall
B. Wireshark
C. autopsy
D. SHA512
E. IPS
Answer: AE
QUESTION 54
A European-based advertisement company collects tracking information from partner websites and stores it on a local server to provide tailored ads. Which standard must the company follow to safeguard the resting data?
A. HIPAA
B. PCI-DSS
C. Sarbanes-Oxley
D. GDPR
Answer: D
Explanation:
https://www.thesslstore.com/blog/10-data-privacy-and-encryption-laws-every-business-needs-to-know/
QUESTION 55
An organization had a breach due to a phishing attack. An engineer leads a team through the recovery phase of the incident response process. Which action should be taken during this phase?
A. Host a discovery meeting and define configuration and policy updates
B. Update the IDS/IPS signatures and reimage the affected hosts
C. Identify the systems that have been affected and tools used to detect the attack
D. Identify the traffic with data capture using Wireshark and review email filters
Answer: B
QUESTION 56
An engineer is going through vulnerability triage with company management because of a recent malware outbreak from which 21 affected assets need to be patched or remediated. Management decides not to prioritize fixing the assets and accepts the vulnerabilities. What is the next step the engineer should take?
A. Investigate the vulnerability to prevent further spread
B. Acknowledge the vulnerabilities and document the risk
C. Apply vendor patches or available hot fixes
D. Isolate the assets affected in a separate network
Answer: B
Explanation:
Acknowledge issues are those which, for whatever reason, you decide not to resolve at present. There are valid reasons for not immediately resolving a vulnerability, and they should be recorded, along with the reasoning for acknowledging it and a review date given. If the level of risk they present is sufficiently high, record the issue in a risk register.
QUESTION 57
A security engineer deploys an enterprise-wide host/endpoint technology for all of the company’s corporate PCs. Management requests the engineer to block a selected set of applications on all PCs.
Which technology should be used to accomplish this task?
A. application whitelisting/blacklisting
B. network NGFW
C. host-based IDS
D. antivirus/antispyware software
Answer: A
QUESTION 58
Which command does an engineer use to set read/write/execute access on a folder for everyone who reaches the resource?
A. chmod 666
B. chmod 774
C. chmod 775
D. chmod 777
Answer: D
Explanation:
https://www.pluralsight.com/blog/it-ops/linux-file-permissions
QUESTION 59
A SIEM tool fires an alert about a VPN connection attempt from an unusual location. The incident response team validates that an attacker has installed a remote access tool on a user’s laptop while traveling. The attacker has the user’s credentials and is attempting to connect to the network.
What is the next step in handling the incident?
A. Block the source IP from the firewall
B. Perform an antivirus scan on the laptop
C. Identify systems or services at risk
D. Identify lateral movement
Answer: C
QUESTION 60
A threat actor used a phishing email to deliver a file with an embedded macro. The file was opened, and a remote code execution attack occurred in a company’s infrastructure. Which steps should an engineer take at the recovery stage?
A. Determine the systems involved and deploy available patches
B. Analyze event logs and restrict network access
C. Review access lists and require users to increase password complexity
D. Identify the attack vector and update the IDS signature list
Answer: A
QUESTION 61
A patient views information that is not theirs when they sign in to the hospital’s online portal. The patient calls the support center at the hospital but continues to be put on hold because other patients are experiencing the same issue. An incident has been declared, and an engineer is now on the incident bridge as the CyberOps Tier 3 Analyst. There is a concern about the disclosure of PII occurring in real- time. What is the first step the analyst should take to address this incident?
A. Evaluate visibility tools to determine if external access resulted in tampering
B. Contact the third-party handling provider to respond to the incident as critical
C. Turn off all access to the patient portal to secure patient records
D. Review system and application logs to identify errors in the portal code
Answer: C
QUESTION 62
Refer to the exhibit. What results from this script?
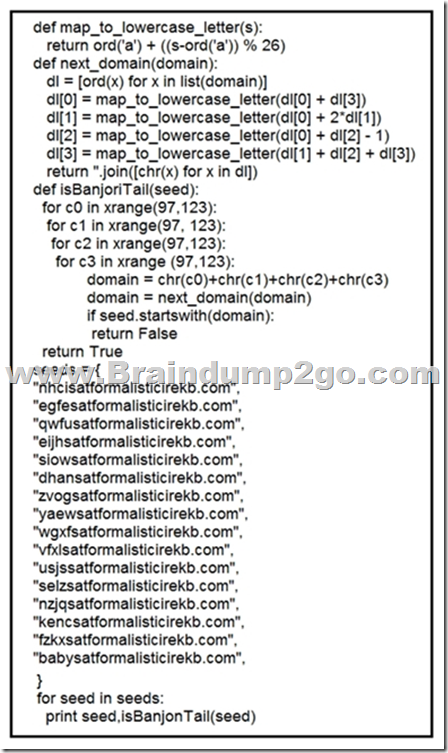
A. Seeds for existing domains are checked
B. A search is conducted for additional seeds
C. Domains are compared to seed rules
D. A list of domains as seeds is blocked
Answer: B
QUESTION 63
Refer to the exhibit. An engineer is reverse engineering a suspicious file by examining its resources. What does this file indicate?
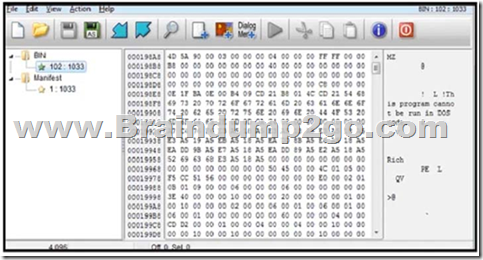
A. a DOS MZ executable format
B. a MS-DOS executable archive
C. an archived malware
D. a Windows executable file
Answer: D
QUESTION 64
Refer to the exhibit. An engineer is performing a static analysis on a malware and knows that it is capturing keys and webcam events on a company server. What is the indicator of compromise?

A. The malware is performing comprehensive fingerprinting of the host, including a processor, motherboard manufacturer, and connected removable storage.
B. The malware is a ransomware querying for installed anti-virus products and operating systems to encrypt and render unreadable until payment is made for file decryption.
C. The malware has moved to harvesting cookies and stored account information from major browsers and configuring a reverse proxy for intercepting network activity.
D. The malware contains an encryption and decryption routine to hide URLs/IP addresses and is storing the output of loggers and webcam captures in locally encrypted files for retrieval.
Answer: D
Explanation:
https://gist.github.com/yetanotherchris/810c5900616b6c76f78dedda9bf3be85
QUESTION 65
An audit is assessing a small business that is selling automotive parts and diagnostic services. Due to increased customer demands, the company recently started to accept credit card payments and acquired a POS terminal. Which compliance regulations must the audit apply to the company?
A. HIPAA
B. FISMA
C. COBIT
D. PCI DSS
Answer: D
Explanation:
https://upserve.com/restaurant-insider/restaurant-pos-pci-compliance-checklist/
QUESTION 66
A customer is using a central device to manage network devices over SNMPv2. A remote attacker caused a denial of service condition and can trigger this vulnerability by issuing a GET request for the ciscoFlashMIB OID on an affected device. Which should be disabled to resolve the issue?
A. SNMPv2
B. TCP small services
C. port UDP 161 and 162
D. UDP small services
Answer: A
Explanation:
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180328-snmp
QUESTION 67
Refer to the exhibit. Which indicator of compromise is represented by this STIX?

A. website redirecting traffic to ransomware server
B. website hosting malware to download files
C. web server vulnerability exploited by malware
D. cross-site scripting vulnerability to backdoor server
Answer: B
QUESTION 68
Refer to the exhibit. What is occurring in this packet capture?
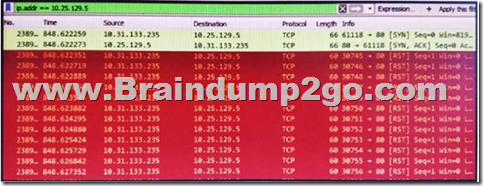
A. TCP port scan
B. TCP flood
C. DNS flood
D. DNS tunneling
Answer: B
QUESTION 69
Refer to the exhibit. How must these advisories be prioritized for handling?
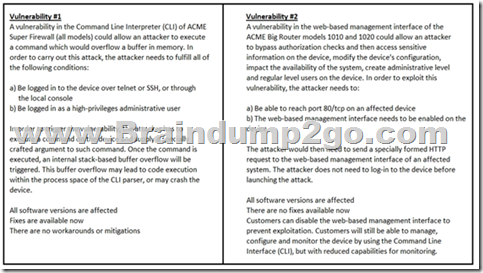
A. The highest priority for handling depends on the type of institution deploying the devices
B. Vulnerability #2 is the highest priority for every type of institution
C. Vulnerability #1 and vulnerability #2 have the same priority
D. Vulnerability #1 is the highest priority for every type of institution
Answer: B
Explanation:
All that is needed is port 80 access on #2 whereas #1 requires a login by a privileged account to exploit.
QUESTION 70
The incident response team receives information about the abnormal behavior of a host. A malicious file is found being executed from an external USB flash drive. The team collects and documents all the necessary evidence from the computing resource. What is the next step?
A. Conduct a risk assessment of systems and applications
B. Isolate the infected host from the rest of the subnet
C. Install malware prevention software on the host
D. Analyze network traffic on the host’s subnet
Answer: B
Explanation:
Short-term containment – limiting damage before the incident gets worse, usually by isolating network segments, taking down hacked production server and routing to failover.
QUESTION 71
An organization had several cyberattacks over the last 6 months and has tasked an engineer with looking for patterns or trends that will help the organization anticipate future attacks and mitigate them. Which data analytic technique should the engineer use to accomplish this task?
A. diagnostic
B. qualitative
C. predictive
D. statistical
Answer: C
Explanation:
What Is Predictive Analytics?
When you know what happened in the past and understand why it happened, you can then begin to predict what is likely to occur in the future based on that information. Predictive analytics takes the investigation a step further, using statistics, computational modeling, and machine learning to determine the probability of various outcomes.
What Is Diagnostic Analytics?
Once you know what happened, you’ll want to know why it happened. That’s where diagnostic analytics comes in. Understanding why a trend is developing or why a problem occurred will make your business intelligence actionable. It prevents your team from making inaccurate guesses, particularly related to confusing correlation and causality.
QUESTION 72
A malware outbreak is detected by the SIEM and is confirmed as a true positive. The incident response team follows the playbook to mitigate the threat. What is the first action for the incident response team?
A. Assess the network for unexpected behavior
B. Isolate critical hosts from the network
C. Patch detected vulnerabilities from critical hosts
D. Perform analysis based on the established risk factors
Answer: B
QUESTION 73
Refer to the exhibit. Cisco Advanced Malware Protection installed on an end-user desktop automatically submitted a low prevalence file to the Threat Grid analysis engine. What should be concluded from this report?
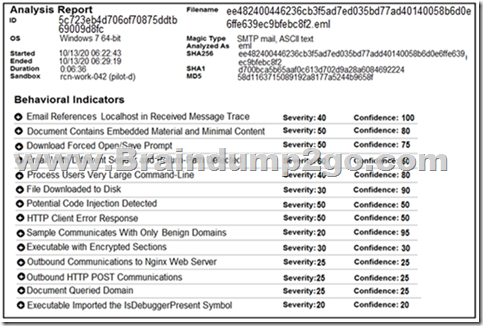
A. Threat scores are high, malicious ransomware has been detected, and files have been modified
B. Threat scores are low, malicious ransomware has been detected, and files have been modified
C. Threat scores are high, malicious activity is detected, but files have not been modified
D. Threat scores are low and no malicious file activity is detected
Answer: D
QUESTION 74
An organization is using a PKI management server and a SOAR platform to manage the certificate lifecycle. The SOAR platform queries a certificate management tool to check all endpoints for SSL certificates that have either expired or are nearing expiration. Engineers are struggling to manage problematic certificates outside of PKI management since deploying certificates and tracking them requires searching server owners manually. Which action will improve workflow automation?
A. Implement a new workflow within SOAR to create tickets in the incident response system, assign problematic certificate update requests to server owners, and register change requests.
B. Integrate a PKI solution within SOAR to create certificates within the SOAR engines to track, update, and monitor problematic certificates.
C. Implement a new workflow for SOAR to fetch a report of assets that are outside of the PKI zone, sort assets by certification management leads and automate alerts that updates are needed.
D. Integrate a SOAR solution with Active Directory to pull server owner details from the AD and send an automated email for problematic certificates requesting updates.
Answer: D
QUESTION 75
Refer to the exhibit. Which data format is being used?
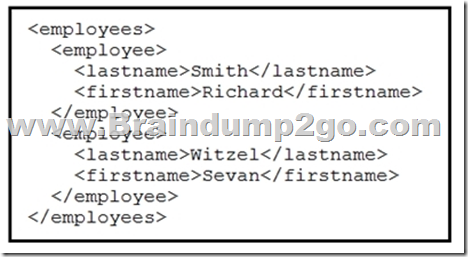
A. JSON
B. HTML
C. XML
D. CSV
Answer: C
QUESTION 76
The incident response team was notified of detected malware. The team identified the infected hosts, removed the malware, restored the functionality and data of infected systems, and planned a company meeting to improve the incident handling capability. Which step was missed according to the NIST incident handling guide?
A. Contain the malware
B. Install IPS software
C. Determine the escalation path
D. Perform vulnerability assessment
Answer: A
Resources From:
1.2023 Latest Braindump2go 350-201 Exam Dumps (PDF & VCE) Free Share:
https://www.braindump2go.com/350-201.html
2.2023 Latest Braindump2go 350-201 PDF and 350-201 VCE Dumps Free Share:
https://drive.google.com/drive/folders/1AxXpeiNddgUeSboJXzaOVsnt5wFFoDnO?usp=sharing
Free Resources from Braindump2go,We Devoted to Helping You 100% Pass All Exams!